Embracing Cybersecurity through Human-Centered Design
April 5, 2024
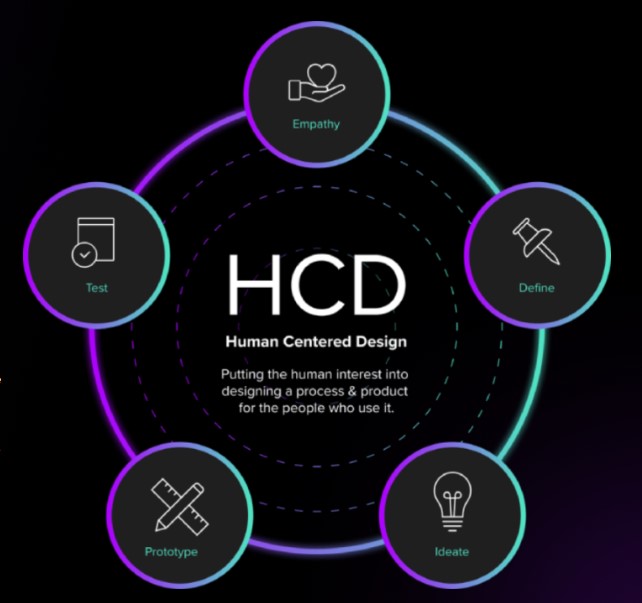
In the rapidly evolving landscape of cybersecurity, the importance of designing systems and solutions with the end user in mind cannot be overstated. Human-centered design (HCD) is a holistic approach that places the needs, capabilities, and experiences of users at the forefront of the design process. In this blog post, we will delve into the concept of human-centered design and explore its five phases, emphasizing how this approach can enhance cybersecurity measures.
Defining Human-Centered Design:
Human-centered design is a problem-solving methodology that prioritizes empathy, collaboration, and iteration to create products, systems, or processes that meet the specific needs and preferences of users. In the context of cybersecurity, this means tailoring security measures to human behavior and ensuring that individuals can seamlessly integrate security practices into their daily routines.
The 5 Phases of Human-Centered Design:
- Empathy:
The first phase of human-centered design involves gaining a deep understanding of the users and their unique challenges. In the realm of cybersecurity, this could entail conducting user interviews, surveys, or observations to identify potential vulnerabilities, user habits, and pain points related to security practices. By empathizing with users, designers can uncover insights that inform the development of more effective and user-friendly security solutions.
- Define:
Once key insights have been gathered, the next step is to define the problem space. This involves synthesizing the information collected during the empathy phase to distill the core issues and challenges faced by users. For cybersecurity, this could involve identifying common threats, user misconceptions, or barriers preventing individuals from adopting secure practices. Clearly defining the problem lays the foundation for targeted and impactful design solutions.

- Ideate:
During the ideation phase, designers generate a multitude of creative solutions to address the defined problems. Brainstorming sessions, collaborative workshops, and design thinking exercises can be employed to encourage diverse perspectives and innovative ideas. In the context of cybersecurity, this might involve developing user-friendly authentication methods, intuitive security interfaces, or interactive educational resources to enhance user awareness.
- Prototype:
With potential solutions in mind, the next step is to create prototypes that represent tangible manifestations of the proposed designs. These prototypes can take various forms, from interactive mock-ups to simplified versions of the final product. In the realm of cybersecurity, prototypes might include user interfaces for security applications, educational modules, or simplified versions of secure workflows. Prototyping allows for early testing and validation of design concepts.
- Test:
The final phase involves gathering feedback from users through testing and refinement. This iterative process ensures that the designed solutions align with user expectations and effectively address the identified challenges. In cybersecurity, testing might involve simulated phishing exercises, usability testing of security interfaces, or assessments of user comprehension through educational materials. Regular testing and refinement are crucial to creating resilient and user-friendly cybersecurity measures.

By incorporating human-centered design principles into cybersecurity practices, organizations can develop solutions that not only enhance security but also prioritize user experience. The five phases of human-centered design provide a structured framework for creating effective and user-friendly cybersecurity measures, ultimately fostering a more secure digital environment for individuals and organizations alike.
Have Any Question?
Call or email Cocha. We can help with your cybersecurity needs!
- (281) 607-0616
- info@cochatechnology.com




