The Silent Battlefield of the Digital Age
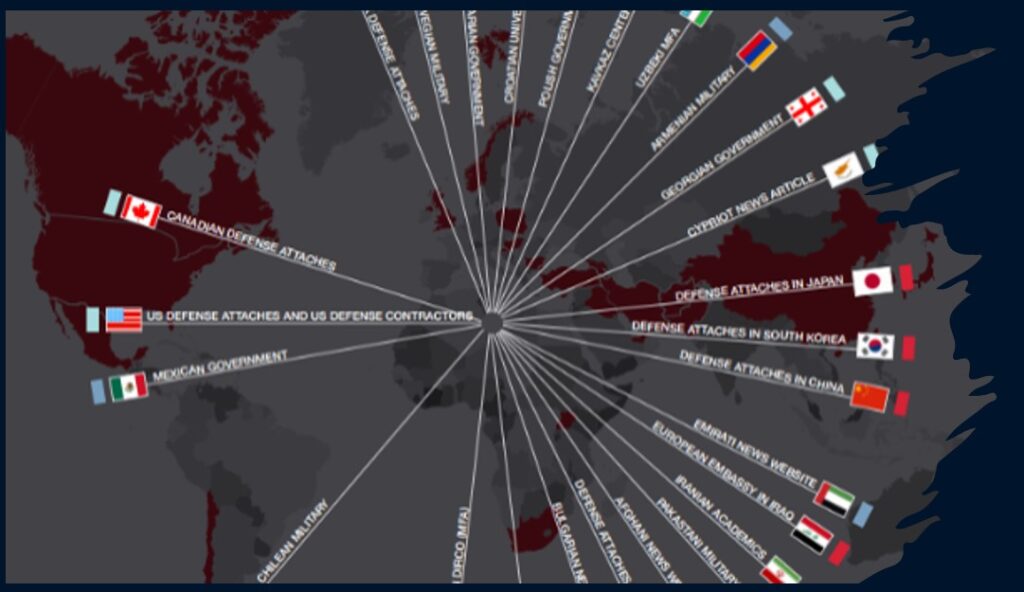
The Silent Battlefield of the Digital Age November 5, 2024 In our increasingly interconnected world, where data is as valuable as gold, a new type of warfare has emerged- cyberwarfare. Unlike traditional forms of conflict, this battlefield is largely invisible, conducted through networks and algorithms rather than troops and tanks. At the forefront of this […]
A Key to Enhancing Your Online Security

A Key to Enhancing Your Online Security November 1, 2024 At some point, we are sure, you have seen the term “token” come up, but what exactly does it mean? And how can it help you stay secure online? In this blog, we’ll break down the concept of tokens, explore how they work, and explain […]
Digital Mafia: The Rise of Organized Cybercrime

Digital Mafia: The Rise of Organized Cybercrime October 29, 2024 In an era where the internet has become the backbone of global communication, commerce, and innovation, cybercrime has evolved from isolated incidents into a highly organized and sophisticated industry. Organized cybercrime groups, often likened to digital mafias, have become one of the most formidable threats […]
Cryptojacking: A Silent Threat in the Digital Age

Cryptojacking: A Silent Threat in the Digital Age October 25, 2024 In our world today, where digital transactions and online activities have become the norm, cybersecurity threats continue to evolve. One such threat that has gained prominence in recent years is cryptojacking. This stealthy form of cyber-attack involves hijacking a device’s computational resources to mine […]
The World of Hackers and How Cybercrime Impacts You

The World of Hackers and How Cybercrime Impacts You October 22, 2024 In the early days of the internet, hackers were often portrayed as lone wolves, motivated by curiosity or the thrill of bypassing digital defenses. Fast forward to today, and the landscape of cybercrime has shifted dramatically. The modern hacker is often part of […]
What You Need to Know About Smartphone Security

What You Need to Know About Smartphone Security October 18, 2024 Today, smartphones have become an extension of ourselves. From communication and entertainment to banking and personal management, our phones hold vast amounts of sensitive information. While these devices offer immense convenience, they also present significant cybersecurity risks. Understanding these risks and knowing how to […]
How Computer Crashes Can Feed Hackers’ Appetite
How Computer Crashes Can Feed Hackers’ Appetite October 15, 2024 Computer crashes, those frustrating moments when your system freezes or unexpectedly shuts down, are not just a nuisance—they can also be exploited by hackers to gain unauthorized access or disrupt operations. In this blog, we delve into the relationship between computer crashes and cybersecurity, exploring […]
Cyber Security: How Honeypots Lure Cyber Attackers

Cyber Security: How Honeypots Lure Cyber Attackers October 11, 2024 In cyber security, one of the most intriguing defensive tools available to organizations is the honeypot. A honeypot is essentially a trap set to detect, deflect, or study attempts at unauthorized use of information systems. But how exactly does this technology work, and why is […]
Understanding the Role of Honeypots in Cyber Security
Understanding the Role of Honeypots in Cyber Security October 8, 2024 In cyber security, where organizations constantly battle against sophisticated threats and malicious actors, innovative defensive measures are crucial. One such tool gaining prominence is the honeypot—a strategic cybersecurity resource designed not to fend off attacks but to attract and deceive potential intruders. Let’s delve […]
Understanding Umbrella Monitoring: Is It Right for You?

Understanding Umbrella Monitoring: Is It Right for You? October 4, 2024 In the age of technological advancement, where threats are constantly evolving, organizations must adopt proactive measures to protect their networks and sensitive data. One such measure gaining prominence is umbrella monitoring. This approach involves comprehensive oversight of network activities, focusing on DNS (Domain Name […]
