Multi-Factor Authentication (MFA): Strengthening Your Online Security
May 30, 2023

In today’s digital landscape, relying solely on passwords for online security is no longer enough. Cybercriminals are becoming more sophisticated, making it crucial to adopt additional layers of protection. Enter Multi-Factor Authentication (MFA), a powerful security measure that significantly enhances your online defenses. In this blog post, we will explore what MFA is, how it works, and provide you with a comprehensive guide to implementing MFA for robust online security.
Understanding Multi-Factor Authentication (MFA)
MFA is a security mechanism that requires users to provide two or more different forms of identification to access an account or system. By combining multiple factors, such as something you know (password), something you have (smartphone), or something you are (biometrics), MFA adds an extra layer of protection against unauthorized access.
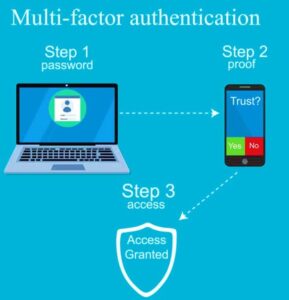
Benefits of MFA
Implementing MFA offers several advantages, including:
Enhanced Security: MFA adds an extra layer of protection, making it significantly harder for cybercriminals to gain unauthorized access to your accounts.
Mitigating Password Vulnerabilities: Since MFA requires an additional factor beyond a password, it helps address the inherent weaknesses of passwords, such as reuse, weak passwords, or phishing attacks.
Increased User Confidence: By utilizing MFA, users can feel more confident that their accounts are better protected, reducing the risk of identity theft or data breaches.
Choosing the Right MFA Method
There are various MFA methods available, and choosing the most suitable option depends on your needs and preferences. Common MFA methods include:
Authenticator Apps: Apps like Google Authenticator, Microsoft Authenticator, or Authy generate time-based OTP codes.
SMS-based OTP: One-time passwords sent via text messages to your registered mobile number.
Hardware Tokens: Physical devices that generate unique codes, often used in high-security environments.
Biometrics: Utilizing fingerprint, facial recognition, or iris scans for authentication.
Implementing MFA
Here’s a step-by-step guide to implementing MFA:
Identify critical accounts: Start by identifying the accounts that hold sensitive information or have access to critical systems.
Enable MFA: Look for the MFA settings within each account’s security settings. Follow the provided instructions to enable MFA and select your preferred method.
Configure Authenticator App: If opting for an authenticator app, download and install the app of your choice on your smartphone. Follow the app’s instructions to scan the QR code provided by the account you’re setting up.
Test the Setup: Once MFA is enabled, log out of the account and attempt to log back in. You’ll be prompted to provide the additional factor for authentication. Verify that everything is working correctly before relying on MFA for regular use.
Best Practices for MFA
To ensure the effectiveness of MFA, consider the following best practices:
Enable MFA on all relevant accounts: Utilize MFA on your email, social media, financial, and any other accounts that support it.
Use unique authentication factors: Avoid using the same factor, such as SMS-based OTP, for multiple accounts. Diversify your MFA methods to add an extra layer of security.
Keep backup options: Always have a backup method configured in case your primary MFA method becomes unavailable or compromised.
Regularly review MFA settings: Periodically review your MFA settings to ensure they are up to date, removing any unnecessary or outdated methods.
Multi-Factor Authentication (MFA) is an essential security measure that significantly strengthens your online defenses. By implementing MFA and using multiple authentication factors, you can mitigate the risks associated with password vulnerabilities and enhance the security of your accounts. Take control of your online security today by enabling MFA wherever possible and enjoy greater peace of mind in an increasingly interconnected world. Stay secure!
Have Any Question?
Call or email Cocha. We can help with your cybersecurity needs!
- (281) 607-0616
- info@cochatechnology.com




