Cloud Security
Our evaluation will test and analyze your organization’s cloud infrastructure to ensure your system is protected from a variety of security risks and threats.
Get Your Free Security Review
Complete Cocha’s online cybersecurity questionnaire today and see how safe your organization’s data is.

Cloud Security
Cocha Technology will help your organization review your cloud security posture, make recommendations for improvement, and oversee the improvement efforts with both your internal team and Cocha’s resources.
Cloud security refers to a set of measures and technologies put in place to protect cloud-based data, applications and infrastructure from unauthorized access, theft, and cyber-attacks. Cloud security is essential for organizations that store, process, and transmit sensitive data in hte cloud. Cocha can help design, build and operate your cloud security and cloud posture management.
Overview of Services
The services Cocha provides focuses on the following areas, and there is design, build, and operational components of each one:
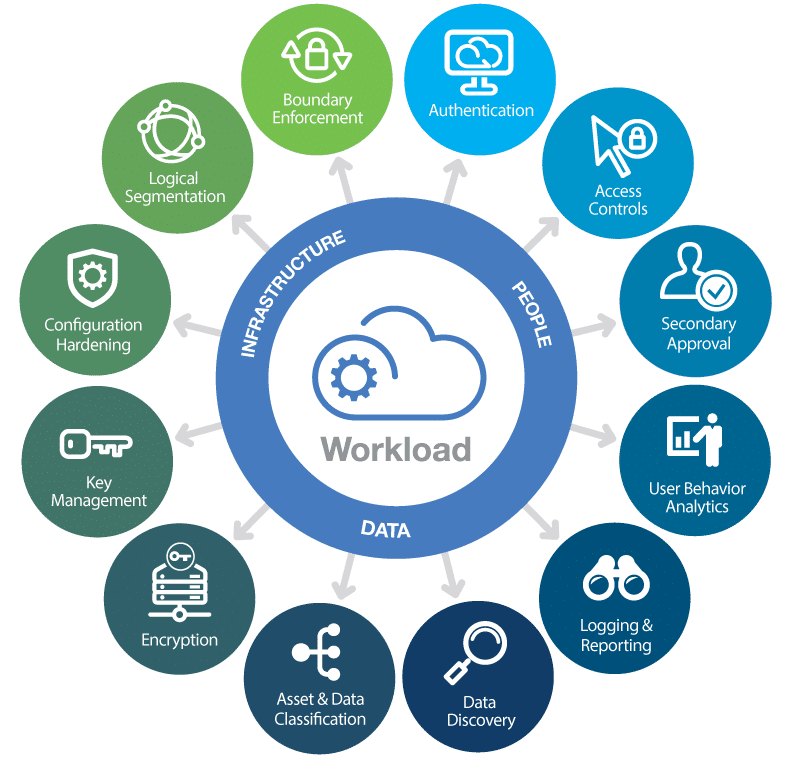
Access Control: Access control is a critical component of cloud security that restricts user access to cloud resources based on their roles and responsibilities. This helps to prevent unauthorized access to sensitive data and applications. Access control can be implemented through various mechanisms, such as role-based access control (RBAC) and multi-factor authentication (MFA).
Data Encryption: Data encryption is the process of encoding data so that it can only be accessed by authorized users who have the decryption key. Encryption is an important aspect of cloud security as it protects data from theft or unauthorized access during transit and at rest. Encryption can be implemented at various levels, such as data-at-rest encryption, data-in-motion encryption, and encryption of data in use.
Network Security: Network security involves securing the network infrastructure and protocols that support cloud-based applications and services. This includes measures such as firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs) to prevent unauthorized access to cloud resources.
Security Monitoring: Security monitoring involves the continuous monitoring of cloud resources for security threats and vulnerabilities. This can be done through various mechanisms such as security information and event management (SIEM) systems, intrusion detection and prevention systems, and security analytics tools.
Disaster Recovery and Business Continuity: Disaster recovery and business continuity planning are important aspects of cloud security. Organizations should have a plan in place to recover their data and applications in the event of a disaster or service outage. This includes regular backups, replication, and failover mechanisms to ensure business continuity.
Overall, cloud security is a complex and evolving field that requires continuous monitoring, testing, and updating to stay ahead of the latest threats and vulnerabilities. Organizations should work closely with Cocha Technology to ensure that their data and applications are secured to the highest standards.